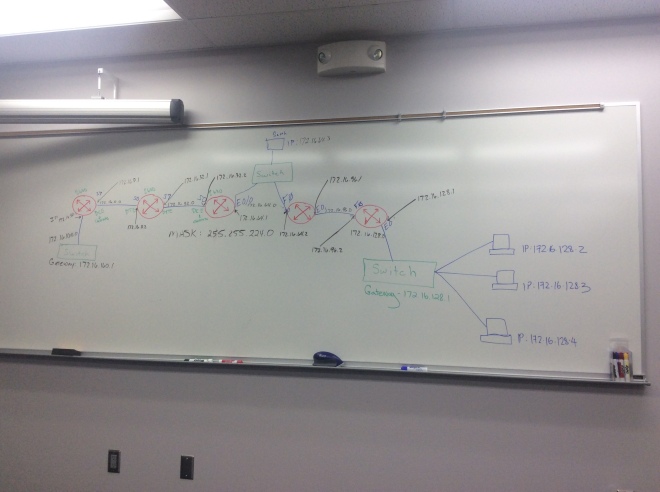
Objectives: To acquire an understanding for the OSI model and get a better understanding of a modern computer network.
Equipment:
- Lab sheet handout
- Computer (any smart device with networking capability)
Notes and Observation:
1. The OSI model was created to define a unifying standard for networking systems. It wasn’t intentional for being an educational tool, but is widely used to describe interactions between the components of other protocols and hardware devices.
2. OSI, stands for Open Systems Interconnection Model. It was originated in 1984, by the ISO and the CCITT.
3. The mnemonic used to aid in assisting OSI layer memorization is “Please Do Not Throw Sausage Pizza Away” (PDNTSPA)
Physical – Hubs and repeaters
Data link – Switches, bridges, and NICs
Network – Routers
Transport – Software based; TCP/IP
Session – Manages connections
Presentation – Provides context
Application – Interacts directly with software and user
4. Highest layer of operation for Following network devices
- Switch-Layer 2
- Hub-Layer 1
- NIC-Layer 2
- Router-Layer 3
- Cable Media-Layer 1
- Wireless Access Point-Layer 2
- Patch Panel-Layer 1
- Repeater-Layer 1
- Bridge 2
What is the purpose and function of…
- Routers-determine where to send information from one computer to another.
- Switches- a device that channels incoming data from any of multiple input ports to a specific output port then will take the data toward its intended destination
- Hubs-commonly used to connect segments of a LAN. A hub contains multiple ports. When a packet arrives at one port, it is copied to the other ports so that all segments of the LAN can see all packets.
5. What is another name of a physical address…
- MAC-Media Control Access (32 Bits)
- NPA- Networking Access Control
- PAC- Physical Address Control
- NAC- Networking Access Control
When two machines attempt to transmit simultaneously on the same media segment, and arrive unintelligible, a Collision has said to have happened.
6. My current desktops (IP)(ipV4) address is
My current MAC address is
The current manufacturer for this device is
- 1156 Aster Ave. Sunnyvale CA 94086-6810 US
7. ARP stands for Address Resolution Protocol.
- Why is a Ping useful?- Provides the ability to make sure there is a connection to the network and that the computers can talk to each other.
- What address is added to arp tables at http://www.sal.ksu.edu? – It provided a gateway address, due to the path it took.
8. Method is used to translate a known layer 3 address into an unknown layer 2 address-
- Address Resolution Protocol
9. Layer 3 gateway devices
- Router
- Firewall
- Layer 3 switch
Operates on a IP, and requires 32 bis.
10. What type of information does a tracert provide?
- It provides the route that a packet takes to get the destination that was designated. It will also show how many routers it when through as well as their response times.
11. What information is provided in the switch MAC address table?
- Displays the port, type and physical address.
Does the MAC address shown in the table match the MAC address of the computer that is connected?
Conclusion:
This was a fun lab. I have not really had much experience pinging computers and locating IP addresses. So that was informative and interesting . I feel I was able to gain a better understanding of how hubs, switches, and routers function on a network. How they direct traffic, and the role that layers play in operating that said traffic. I feel I have a broader understanding now of the OSI model and how it applies to a network.


















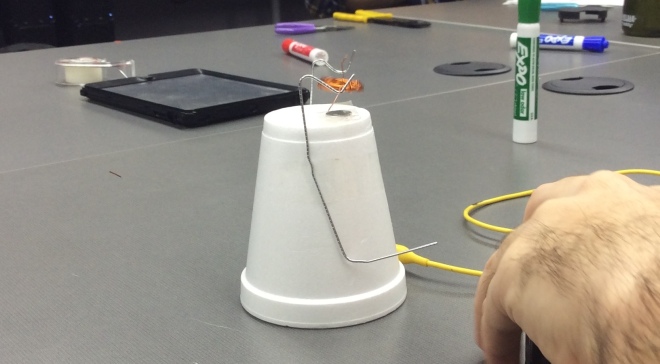
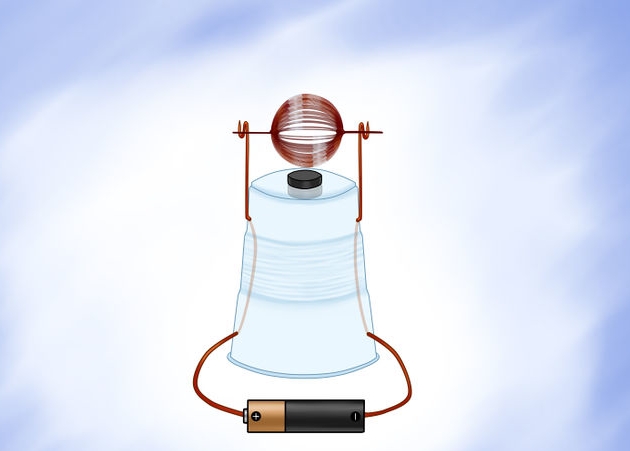
 It is recommend that you wrap it around 15-20 times. You will also need to leave about 2 inches on each side of the armature coil. When completed it should look similar to this.
It is recommend that you wrap it around 15-20 times. You will also need to leave about 2 inches on each side of the armature coil. When completed it should look similar to this. 
 It is important to note that when you begin scraping the insulation coating. You need only scrape the top half of the wire. Leaving the insulation on the the other side. If done correctly one side will look really shiny.
It is important to note that when you begin scraping the insulation coating. You need only scrape the top half of the wire. Leaving the insulation on the the other side. If done correctly one side will look really shiny.